Organization and Account Structure⚓︎
Overview⚓︎
Landing Zone Accelerator uses AWS Accounts to enforce strong isolation between teams, business units and application functions. The sections below discuss the account design, the sample configuration files create through, AWS Control Tower or AWS Organizations.
Organization structure⚓︎
The Landing Zone Accelerator includes the following default AWS organization and account structure.
Note: the AWS account structure is strictly a control plane concept - nothing about this structure implies anything about the network architecture or network flows.
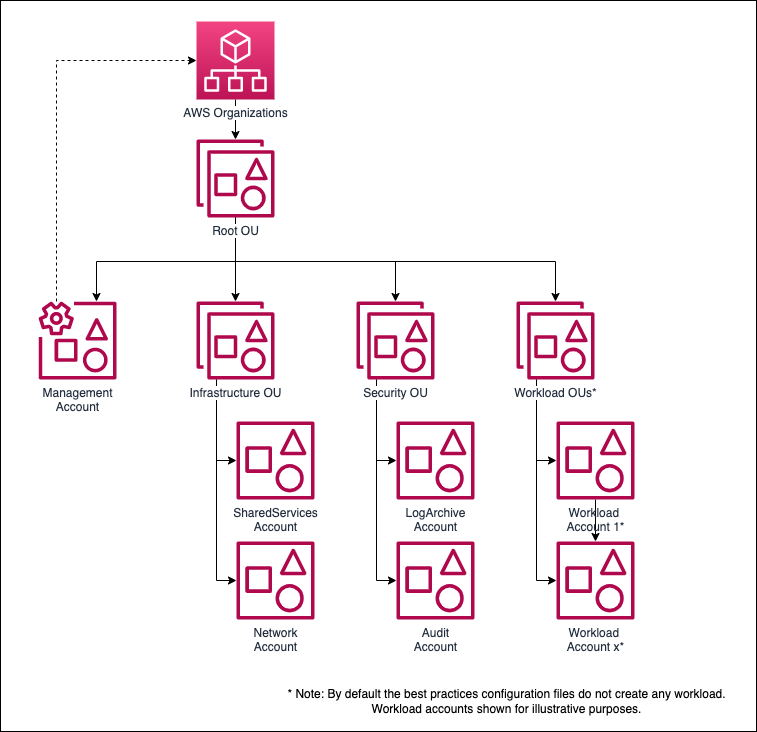
Organization Management (root) AWS Account⚓︎
The AWS Organization resides in the Organization Management (root) AWS account and is traditionally an organization's first AWS account. This account is not used for workloads - it functions primarily as a billing aggregator, and a gateway to the entire cloud footprint for high-trust principals. Additionally, the Organization Management account is where the automation engine or tooling is installed to automate the deployment of the LZA architecture and its security guardrails. As per the best practices resources described above, access to this account must be carefully governed.
Organizational Units⚓︎
Underneath the root of the organization, Organizational Units (OU) (OUs) provide a mechanism for grouping accounts into logical collections. LZA makes use of OUs to enforce specific preventative controls through service control policies (SCPs), resource sharing across the organization through Resource Access Manager, and the ability to apply LZA configurations to groups of accounts e.g. a specific network pattern deployment.
The Default sample configuration files OU structure is shown below:
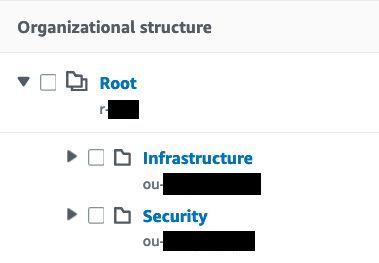
For further details to help you plan your OU structure beyond the defaults provided by these configuration files, review the best practices for organizational units and also the recommendations on OUs and accounts.
Security OU⚓︎
The accounts in this OU are considered administrative in nature with access often restricted to IT security personnel. The sample configuration files add two accounts to this OU:
Infrastructure OU⚓︎
The accounts in this OU are also considered administrative in nature with access often restricted to IT operations personnel. The sample configuration files add two accounts to this OU:
Core Accounts⚓︎
Core accounts can be defined as accounts that have special significance within the organization. Often these will provide functions shared across accounts within the organization, for example, centralized logging or network services.
The Landing Zone Accelerator deployment enforces a subset of core accounts as defined in the mandatory accounts section of the implementation guide. The sample configuration adds additional core accounts for the specific functions listed below.
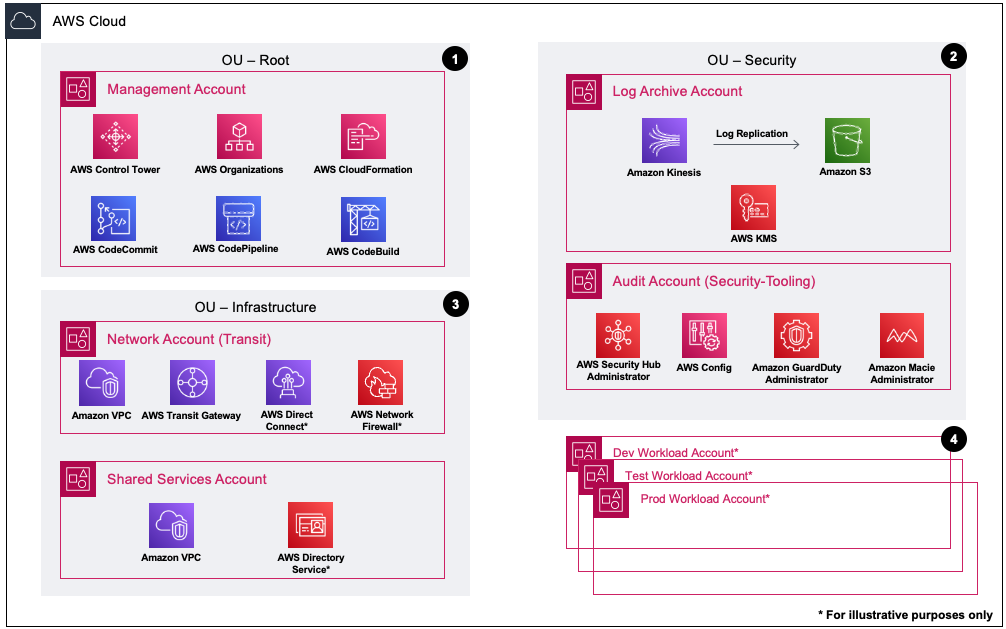
- Management account
- Audit account (Security Tooling)
- Log Archive account
- Network account (Transit)
- Shared Services account
Workload Accounts⚓︎
Workload (Application) accounts are created on demand and placed into an appropriate OU in the organization structure. The purpose of workload accounts is to provide a secure and managed environment where project teams can use AWS resources. They provide an isolated control plane so that the actions of one team in one account cannot inadvertently affect the work of teams in other accounts.
Account Level Security Settings⚓︎
The LZA sample configuration files enable certain account-wide features on account creation. Namely, these include:
- S3 Public Access Block
- Default encryption of EBS volumes using a customer managed local account KMS key
- Tagging policy applied to the root OU via the organization-config.yaml taggingPolicies key. To help you define a tagging policy that meets your organizations see AWS tagging best practices. You can then amend the example tagging policy provided by these configuration files.
- Backup Policy applied to the root OU via the organization-config.yaml backupPolicies key.