Automated Deployment
Before you launch the solution, review the architecture, supported regions, and other considerations discussed in this guide. Follow the step-by-step instructions in this section to configure and deploy the solution into your account.
Time to deploy: Approximately 15 minutes
Note
Before deploying this solution, we recommend you create a billing alarm to monitor your estimated AWS charges.
The user or IAM role to perform the deployment must have at least permissions defined in the permissions.json file. If you use the permissions defined in this file to deploy this solution, your CloudFormation stack name should start with QCEDD, for example, QCEDDStack.
Prerequisites
If bellow steps have already been done, please skip this section.
Preparation: Enable Amazon Braket service
-
Log into the AWS Management Console, and go to Amazon Braket console.
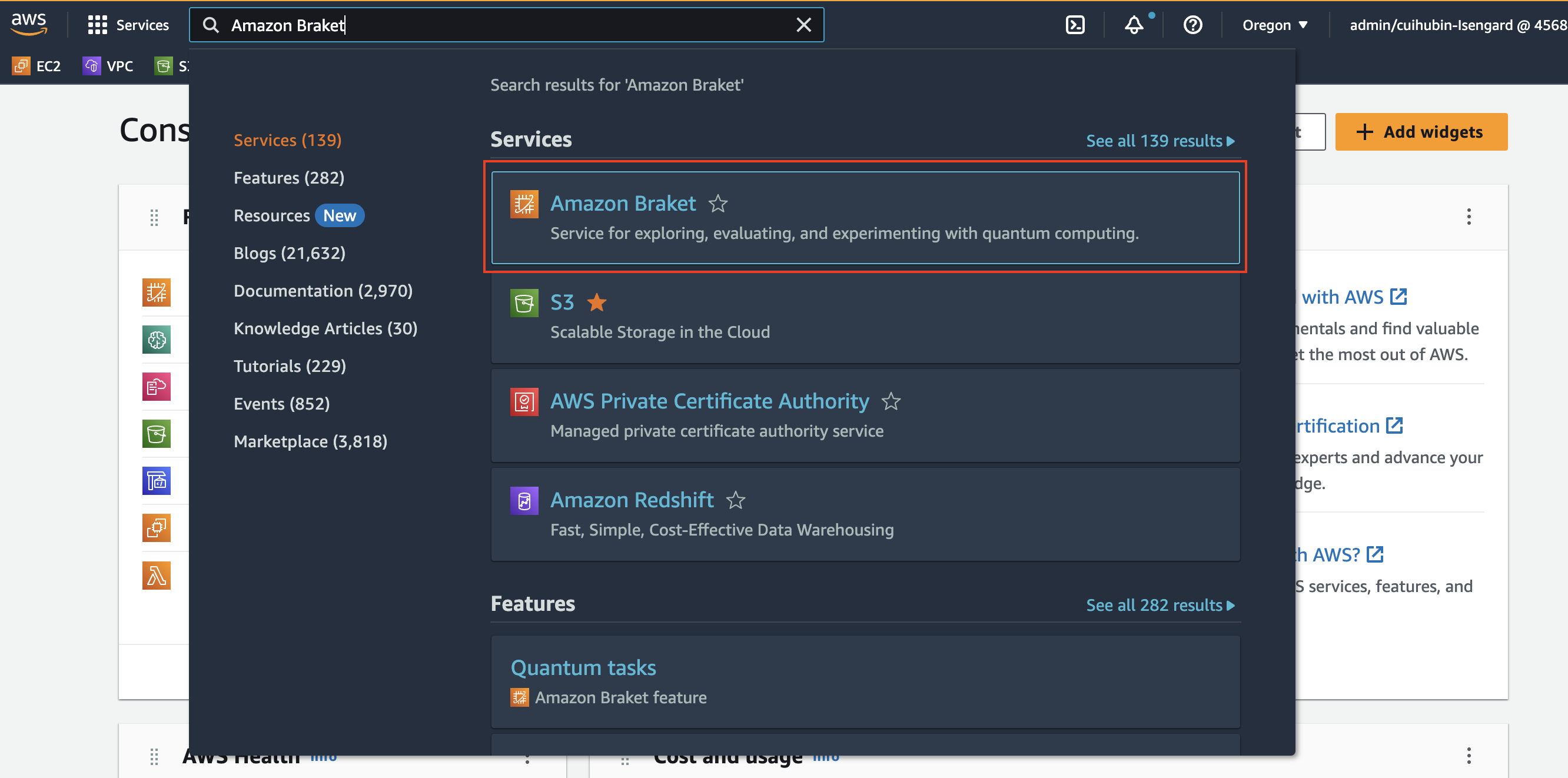
-
Choose Permissions and Settings in the left navigation pane, then choose the General tab, and choose Accept and Enable
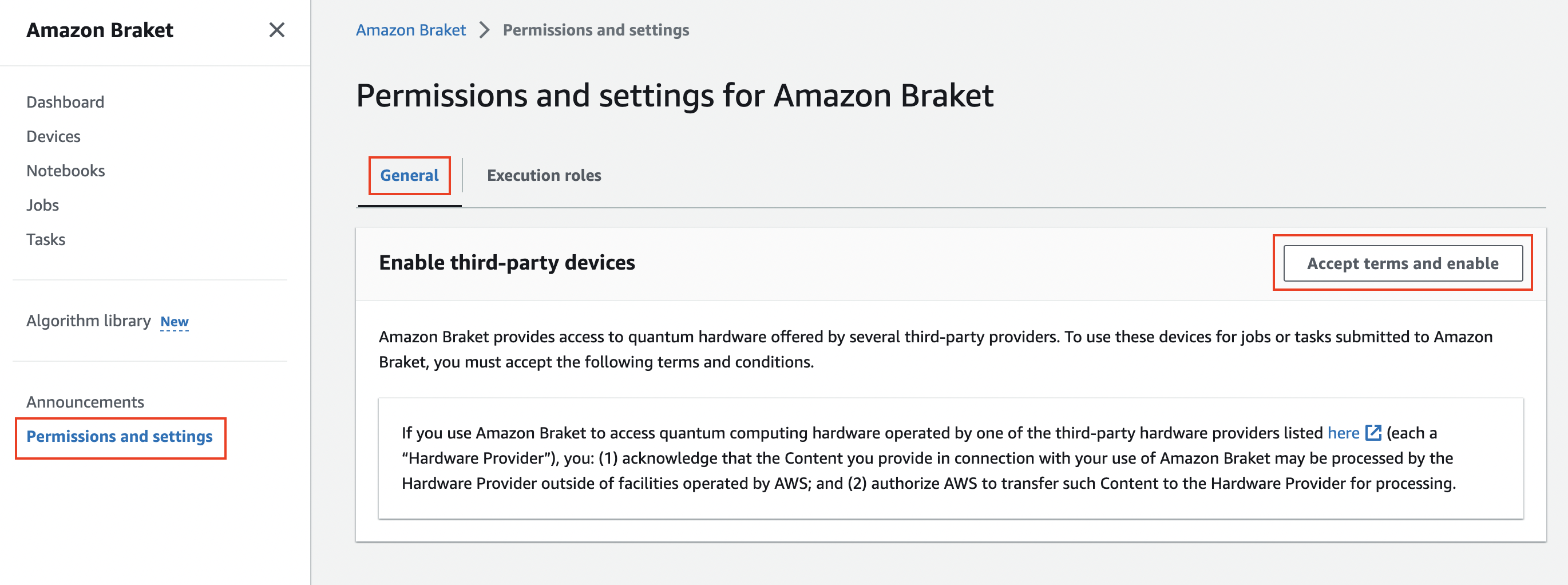
-
Choose the Execution Roles tab, and choose Create Service-linked Role to create service-linked role.
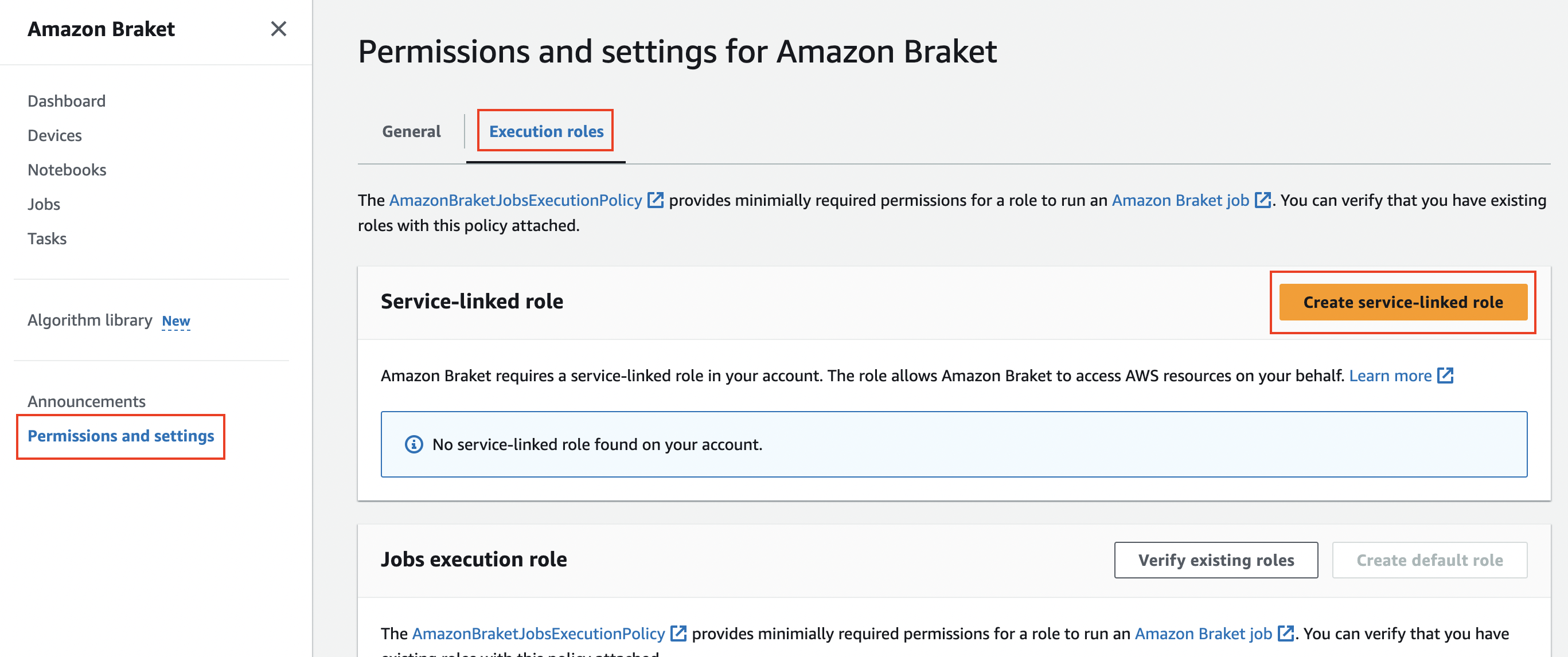
-
Choose Verify Existing Roles to create jobs execution role.
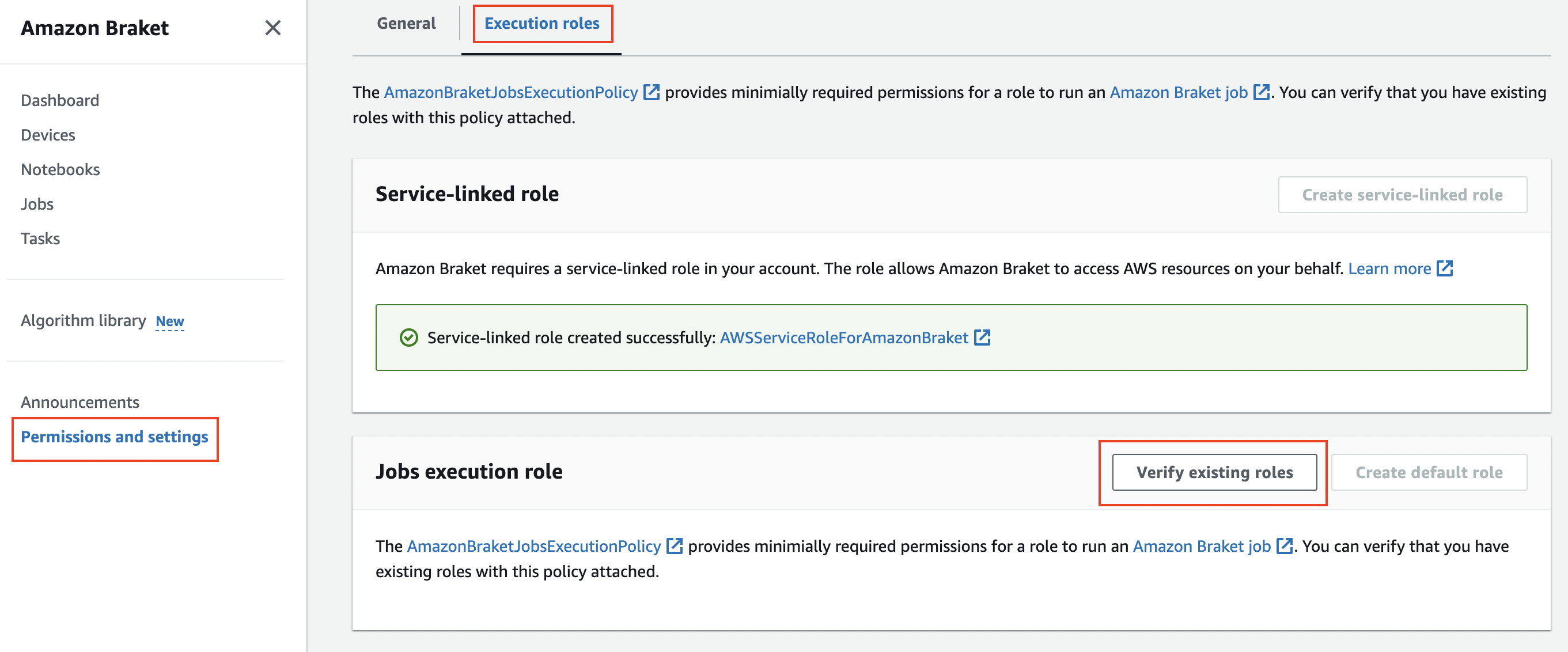
Step 1: Launch the AWS CloudFormation template into your AWS account
-
Sign in to the AWS management console, and select the Launch solution button to launch the AWS CloudFormation template. Alternatively, you can download the template as a starting point for your own implementation.
-
The template launches in the US West (Oregon) by default. To launch this solution in a different AWS Region, use the Region selector in the console navigation bar.
-
On the Create stack page, verify that Amazon S3 URL is filled with this template URL automatically and choose Next.
-
On the Specify stack details page, assign a name to your solution stack. For information about naming character limitations, refer to IAM and STS Limits in the AWS Identity and Access Management User Guide.
-
Under Parameters, review the parameters for the template and modify them as necessary.
This solution uses the following parameters.
Parameter Default Description snsEmail null email for subscribe message -
Choose Next.
-
On the Configure stack options page, choose Next.
-
On the Review page, review and confirm the settings. Check the box acknowledging that the template will create AWS Identity and Access Management (IAM) resources.
-
Choose Create stack to deploy the stack.
-
If you configured a subscription email, please pay attention to the email inbox, and then click the Confirm Subscription link to confirm the subscription.
You can view the status of the stack in the AWS CloudFormation Console in the Status column. You should receive a CREATE_COMPLETE status in approximately 15 minutes.
Step 2: (Optional) Subscribe to SNS notification
Follow below steps to subscribe to SNS notification via email to receive result notifications from AWS Step Functions. You can also subscribe to the notification via text messages.
-
Sign in to the AWS CloudFormation console.
-
On the Stacks page, select the solution’s root stack.
-
Choose the Outputs tab and record the value for the SNS topic.
-
Navigate to the Amazon SNS console.
-
Choose Topics, then select the SNS topic that you obtained from the CloudFormation deployment output.
-
Choose Create subscription.
-
Select Email from the Protocol list.
-
Enter your email in Endpoint.
-
Choose Create subscription.
-
Check your mailbox, you will receive an email, click the Confirm Subscription link in the email to confirm the subscription.
Update AWS CloudFormation template
If needed, you can update the AWS CloudFormation stack to change the deployment settings.
Important
If the content of the notebook algorithm changed, please delete the original CloudFormation and create a new CloudFormation. Updating the CloudFormation will not make your algorithm changes take effect.
-
Sign in to the AWS CloudFormation console.
-
Select the root stack of this solution, not the nested stack.
-
Choose Update.
-
Select Use current template, and choose Next.
-
Update the parameters as needed, and choose Next.
-
On the Configure stack options page, choose Next.
-
On the Review page, review and confirm the settings. Check the box acknowledging that the template will create AWS Identity and Access Management (IAM) resources.
-
Choose Update stack to update the stack.