Configuring Service Workbench using Microsoft Azure AD
Updating accounts
You can use Azure AD to create and manage domains, users, and objects within a network. It provides a way to organize a large number of users into logical groups and subgroups. It also provides access control at each level. For more information about IdPs, see Identity Providers.
Azure AD (or any IdP) is a source of authentication. It authenticates users for Service Workbench login. After successful Azure AD login, it sends user information to an Amazon Cognito user pool created by Service Workbench. Service Workbench then uses the Amazon Cognito user pool for its internal use as described in Service Workbench and IdP workflow.
To configure Azure AD authentication:
- Create an IdP if you don’t have one. For more information about creating an IdP, see sign up your organization.
- Download SAML metadata (XML file).
- Using Amazon Cognito on the AWS Management Console, create an Amazon Cognito user pool. The name of the pool must be
<stage>-<solution_name>-userPool, wherestageandsolution_nameare configured in the main configuration file. - Gather the relying party information, such as
User Pool Id,Relying Party Id, andUser Pool Signing Cert. - Run the following script from the root of Service Workbench repository:
scripts/get-relying-party.sh - Copy the output of this script and provide it to your Azure AD administrator.
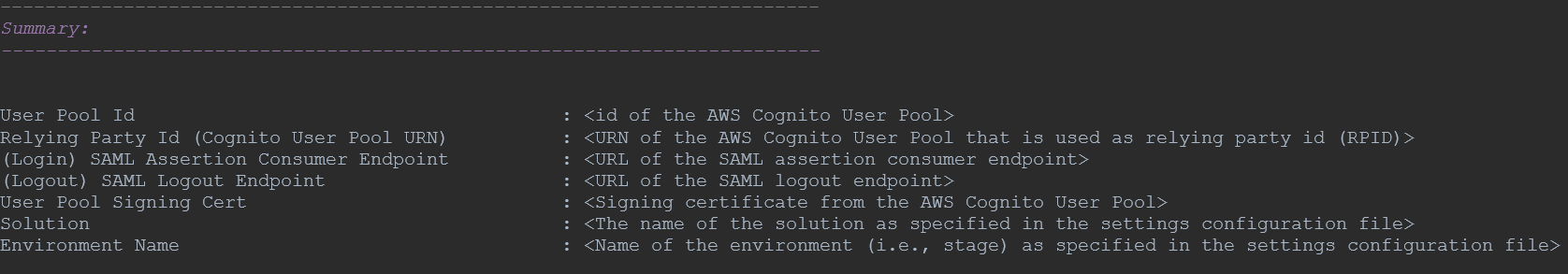
Figure: Script output